In the spirit of Bay Area Crypto Day, NY Crypto Day, and others, Ontario Cryptography Day aims to bring together the cryptography community in Ontario for a day of research talks and discussions. We hope to establish a recurring event rotating through universities in Ontario.
The event is open to academic, industry, and public sector researchers and practitioners in cryptography, but registration is required.
University of Waterloo
Davis Centre (DC) 1301 and 1302
Registration
Registration is now closed
Program
| 09:40–10:00 |
DC 1301 |
Registration |
| 10:00–10:05 |
DC 1302 |
Welcome |
| 10:05–10:40 |
DC 1302 |
Vahid Reza Asadi, University of Waterloo.
Lower Bounds on Entanglement and Quantum Gates in Non-local Quantum Computation
Abstract: A non-local quantum computation (NLQC) replaces an interaction between two quantum systems with a single simultaneous round of communication and shared entanglement. In this talk, we will review two classes of NLQC, f-routing and f-BB84, which are of relevance to classical information-theoretic cryptography and quantum position verification, and we will show the first non-trivial lower bounds on entanglement in both settings, but are restricted to lower bounding protocols with perfect correctness. Within this setting, we give a lower bound on the Schmidt rank of any entangled state that completes these tasks for a given function f(x,y) in terms of the rank of a matrix g(x,y) whose entries are zero when f(x,y)=0, and strictly positive otherwise. This also leads to a lower bound on the Schmidt rank in terms of the non-deterministic quantum communication complexity of f(x,y). We also prove that the number of quantum gates plus single qubit measurements needed to implement a function f is lower bounded linearly by the communication complexity of f in the simultaneous message-passing model with shared entanglement. Because of a relationship between f-routing and the conditional disclosure of secrets (CDS) primitive studied in information-theoretic cryptography, we obtain a new technique for lower bounding the randomness complexity of CDS.
|
| 10:40–11:10 |
DC 1301 |
Coffee break |
| 11:10–11:45 |
DC 1302 |
Connor Paddock, University of Ottawa. Using nonlocal games to verify quantum computation through cryptographic compilation
|
| 11:45–12:20 |
DC 1302 |
Matthew McPherrin, Let's Encrypt.
More than just Signatures: Challenges in operating certificate authorities
Abstract: Certificate Authorities are one of the most widely used trusted third parties. The Web PKI community has recently decided to shorten the lifetime of certificates down to 47 days in the next few years. In this talk we discuss how tradeoffs between engineering constraints, trust in third parties, revocation challenges, and certificate transparency led to that number. Revocation of certificates contains tradeoffs between privacy, security, and efficiency which are significant engineering challenges. Trust in certificate authorities is also helped via the Certificate Transparency log system, which has its own privacy tradeoffs. Finally, we’ll touch on future challenges of bringing post-quantum signatures that will interact with these choices in the future.
|
| 12:20–13:50 |
DC 1301 |
Lunch |
| 13:50–14:50 |
DC 1302 |
Invited keynote: Chris Peikert, University of Michigan. Unexpected Applications of Fully Homomorphic Encryption |
| 14:50–15:20 |
DC 1301 |
Coffee break |
| 15:20–15:55 |
DC 1302 |
Brian Goncalves, Toronto Metropolitan University. DiSK: A Deniable Split KEM from The MLWE Problem
Abstract: As the pending migration away from quantum-vulnerable cryptography becomes a reality, widely used key-exchange protocols like Signal need to be replaced. Given the countless number of people who use applications like Signal and Whatsapp, there is an urgent need to find a suitable replacement to continue protecting messages sent via these apps from becoming exposed. However, in order to be a true successor to protocols such as Signal, all security guarantees provided by it must be maintained. This includes indistinguishability, asynchronicity, and deniability. One tool for finding replacements are deniable split Key Encapsulation Mechanisms (KEMs) as defined by Brendel et al. [8]. Split KEMs are designed to mimic the message structure of Diffie-Hellman-based protocols such as X3DH used in Signal. Collins et al. recently formalized the definition of deniability for split KEMs, providing another step toward split KEMs being practical tools for migration [9]. In this work, we present a new deniable split KEM, which we call DiSK (Deniable Split KEM). Our split KEM is based on the Module Learning With Error problem [6, 20] and the Non-Interactive Key-Exchange (NIKE) SWOOSH [13]. We prove the indistinguishability and deniability of DiSK in the quantum random oracle model with tight security reductions. This is joint work with Atefeh Mashatan.
|
| 15:55–16:30 |
DC 1302 |
Rasoul Akhavan, University of Waterloo.
Overcoming Challenges of Deploying PIR in Real-World Applications
Abstract: Private Information Retrieval (PIR) is a useful privacy-preserving protocol that is broadly applicable as a fundamental building block in various systems due to its generic functionality. While PIR was originally considered impractical for real-world deployment, recent advancements have led to the design of highly efficient PIR protocols. While these significant speed improvements are necessary for practical deployment, many of these protocols rely on assumptions that frequently do not hold in real-world applications. This talk will explore specific real-world applications of PIR, such as its use within the InterPlanetary File System (IPFS), and highlight the challenges these applications present for integrating existing PIR schemes. Motivated by these practical considerations, we will present our recent work on PIR without setup, among other related contributions. We will detail several novel constructions of PIR that eliminate the need for setup phases and reduce communication costs. We demonstrate how these constructions are specifically designed to align with the assumptions and requirements prevalent in real-world deployments.
|
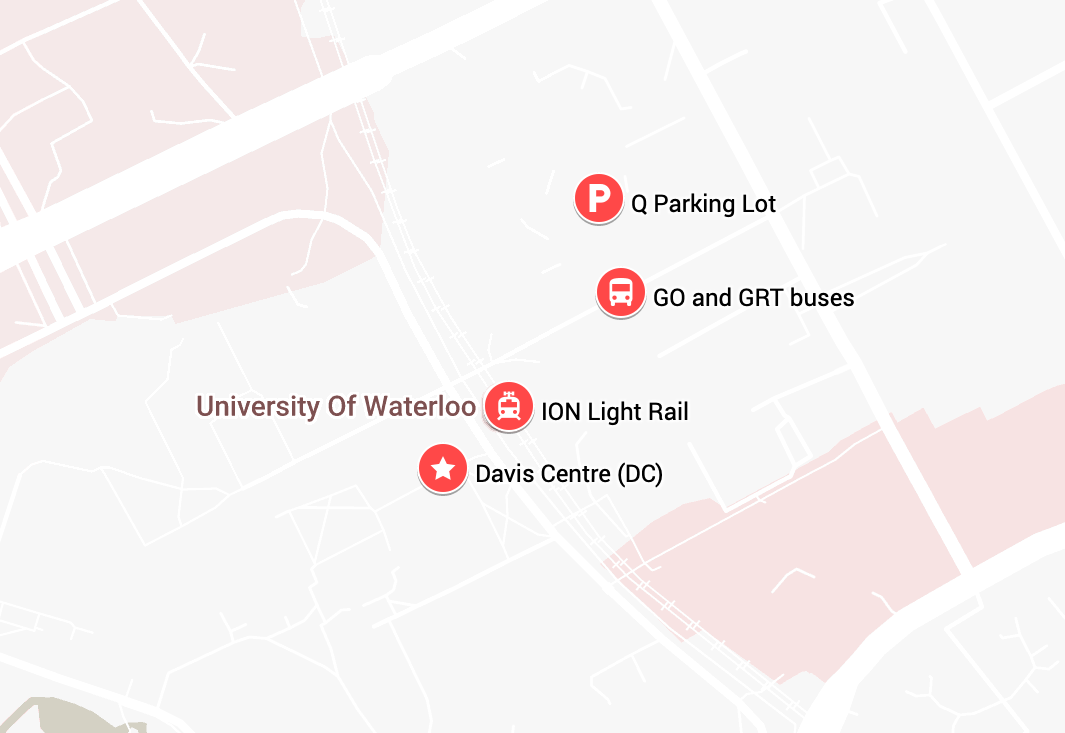
Travel
Parking: The closest visitor parking to the Davis Centre is Q Lot, which costs about $7/day and must be paid using the AMP Mobile pay app.
Public transport:
- GO Transit: Some GO Transit buses come directly to campus. For example, there is a GO train departing Toronto’s Union Station at 7:34am to Bramalea which connects with a GO bus to the University of Waterloo campus, arriving at 9:50am. There are also GO trains to Kitchener station which connect with GRT buses/light rail from Kitchener to UW. Check the trip planner on the GO Transit website for more details.
- Grand River Transit: The ION light rail stops at the University of Waterloo station. There are also many local buses that reach the University of Waterloo campus.
Map
Organizers
For more information, please email dstebila@uwaterloo.ca.
Ontario Cryptography Day was made possible with the financial support of the University of Waterloo’s CryptoWorks21 program, which is housed in the Institute for Quantum Computing and in collaboration with the Cybersecurity and Privacy Institute. Thanks to Sara Zafar Jafarzadeh, Michele Mosca, and Chin Heng Lee for their assistance.

We acknowledge the support of the Natural Sciences and Engineering Research Council of Canada (NSERC).

